من جناح بيلاروسيا
تثبيت التطبيق
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
ملاحظة: This feature may not be available in some browsers.
أنت تستخدم أحد المتصفحات القديمة. قد لا يتم عرض هذا الموقع أو المواقع الأخرى بشكل صحيح.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
متابعة معرض يومكس و سيمتكس 2024
- بادئ الموضوع صقر الامارات
- تاريخ البدء
MILANION تشارك بالعربة الغير مأهولة AGIMA
هل ستفاجئنا EDGE بمنتجات وابتكارات جديدة !!
اتطلع لرؤية جديد الجنية .. خصوصا الجنية 2
اتطلع لرؤية جديد الجنية .. خصوصا الجنية 2
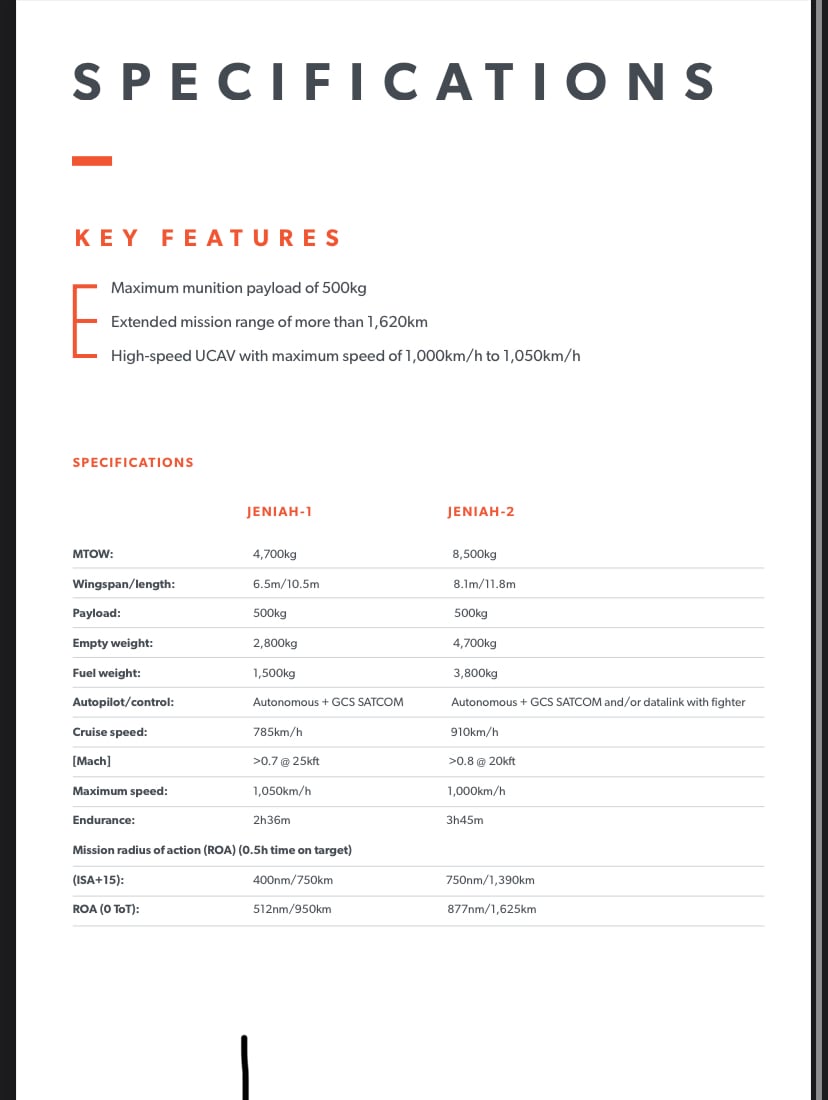
هناك جنيتان بحسب البروشر الخاص بالشركة تم ذكر بقائيتها في الجو (endurance)
جنية-1
بقائية 2:36 ساعة في الجو
نطاق عمليات يبلغ 950 كم مع 30 دقيقة فوق الهدف
جنية-2
بقائية 03:45 ساعة في الجو
نطاق عمليات يبلغ 1625 كم مع 30 دقيقة فوق الهدف
شركة Rosoboronexport تشارك في معرض UMEX 2024
شركة اعتماد تحت لواء ايدج غير
اهداف جويه
التعديل الأخير:
منذ استحواذ ايدج على اعتماد القابضة ونحن نرى ابداعات في المنتجات
https://edgegroup.ae/ar/news/edge-acquires-etimad-holding-major-player-uaes-security-solutions-space
قائمة الشركات التابعة لاعتماد (متميزة)
OUR COMPANIES












حلولهم تغطي قطاعات مهمة
In a world where travel and communications cross borders at an unprecedented pace, governments are faced with a formidable challenge: protecting land and maritime borders against threats ranging from illegal crossings, through organized crime and terrorism, to the trafficking of arms, drugs, and people … while still enabling the travel and commerce that are vital to a modern nation. Currently securing thousands of kilometers of borders in a variety of terrains and environments, Etimad’s border solutions provide smart security that safeguards against illegal incursions and activities – while guaranteeing vetted two-way traffic.
Ongoing adaptive allocation of resources based on hierarchic Command &Control structure, mobile sensing capabilities, and intelligence-driven threat assessment.
Operational optimization based on terrain, weather, and available resources.
Adaptation for land and maritime borders as well as open and closed borders.
Reuse of existing infrastructure and components for optimal ROI and resource utilization.

Etimad provides Borders solutions adapted for specific border types, terrains, and populations, supported by the following core products and capabilities:
Law enforcement has traditionally focused on responsive capabilities - solving crimes and apprehending criminals after the fact. Today, trending and prediction capabilities that have been tried and tested in the commercial arena are recruited to the service of civil society and law enforcement. New systems and platforms provide agencies with tools that harness information from sensors, databases, open sources, the web and the general public – and utilize it to predict criminal patterns and prevent incidents before they occur. Etimad provides law enforcement solutions to numerous countries and agencies, enabling authorities to predict and prevent crime, as well as effectively respond to criminal activities and operations. Our solutions combine the principles of community policing, predictive policing, intelligence-led policing and other proven models to allow for optimal exchange of information between relevant authorities, agencies and the public – and increase the affectivity of law enforcement operations.
Predictive dispatching based on crime data fusion and analysis
Empowering the public to take an active role in creating a safer environment via our crowd sourcing and citizen advisory bidirectional communication platforms.
Integration of external video management systems (indoor/ outdoor surveillance).
Cross-agency and platform collaboration for improved filtering and correlation capabilities.

Critical infrastructures, such as energy production facilities, transportation hubs and communication infrastructure are required to ensure the safety and security of employees, assets and the surrounding community –from both internal and external threats. This challenge is complicated by the fact that critical infrastructures are often placed in diverse and remote locations with thousands of employees entering and exiting the facility every day. Etimad critical infrastructure solution are currently securing manned and unmanned sites all over the world, providing maximum protection and safety to the assets, to facility employees, and to nearby civilian population. Our platforms protect onshore, offshore and coastal assets and infrastructures, analyzing fused data from sensors, databases and the web to detect, deter, prevent and manage any breach of security or safety risk.
Multi-layered safety & security platform combining physical and cyber protection, sensor fusion, intelligence and decision support tools, all correlated in a unified situation awareness picture.
Ongoing adaptive allocation of resources based on hierarchic Command & Control structure, mobile sensing capabilities and intelligence – driven threat assessment.
Operational optimization based on terrain, weather, and available resources.

Flexible, scalable Unified Access Management (UAM) system.
Enhanced crisis management, including employee advisories and dissemination via mobile application.
Etimad provides critical infrastructure protection solutions adapted for specific types of assets, terrains and populations, supported by the following core products and capabilities.
The 21st century city is characterized by dynamic and growing concerns from multiple domains – from transportation, through resource management, to crime and terrorism. Compounding the complexity Of these challenges are the multitude of stakeholders within the city environments – and their need to coherently manage current requirements, while preparing for whatever challenges will emerge from new technologies, changing geopolitics and the growing urbanization of global population. Currently deployed in china, the middle east and the Netherlands, Etimad urban management solutions offer municipal and national authorities a complete portfolio of products and solutions for effective managements of today’s – and tomorrows – complex urban environment.
Holistic, integrative approach to management of urban operations and processes.
Integration of multiple domains and cross domain analysis for new insights and multi-agency collaboration.
Utilization of personal platforms (smart phones, tablets, floating car data) for information collection and dissemination.

Enhanced simulation, planning and prediction capabilities for contingency managements, emergency response and risk mitigation.
Reuse of assets / resources such as infrastructure. Sensors and communication networks for faster deployment and cost savings.
21st century cities are growing rapidly, as over half of today’s word’s population inhabits urban settings, Every day, governments and corporations face new challenges and threats that arise in today’s ever-changing, technologically complex landscape, forcing them to seek new approach to managing public safety, security and well-being, Financial and socio-economic concerns, crime control and community safety are key drivers in pursuing new technologies, operational concepts and the ability to mitigate and contain urban risks and threats. Etimad Safe City solution combines cutting-edge technology, data gathering and analytics capabilities, and advanced modeling platforms to help nations, cities and corporations effectively manage and secure urban environments, reduce crime rates and increase the well-being of its citizens and economic growth.

As modern cities grow, geographical distance becomes irrelevant and an increasing volume of vehicles daily overwhelms every nation’s highways, an effective and efficient public transportation system can be immensely significant to a country’s economic growth and well-being. The ability to move large numbers of citizens and travelers within and across cities, swiftly and efficiently, is challenged by increased traffic congestions, long rush hours, pollution, traffic accidents and inefficient response times. Etimad, Intelligent Traffic System provides an integrated real-time view of all transportation elements, including areas of congestion, parking availability and traffic flow, by correlating historic data and future projections, as well as data from existing and dedicated sensors with information-sharing capabilities and multi-agency collaboration.

The traditional cyber security methods have become infective, due to the complexity of 21st century cyber communication. modern infrastructure is challenged by modern threats, and cyber –technologies have been recognized as strategic weapons and a means to assault critical national infrastructures and assets. In its simplest terms, cyber –security refers to defenses against electronic attacks launched via computer systems. Operational cyber-security encompasses the full range of threat and vulnerability reduction, deterrence, international engagement, incident response, and resiliency, and therefore, requires effective recovery policies and activities, such as security network operations, information assurance, law enforcement, and intelligence missions as they relate to the security and stability of the global information and communication infrastructure. In our expanding digital world, there are multiple types of cyber-attack that include cyber espionage, the disruption of critical infrastructure, compromised equipment, disinformation propaganda and vandalism, and reconnaissance via target systems (which lead to data leaks and compromised intelligence). There are multiple weapons involved in cyber-attacks, which include botnets, email viruses, spyware, worms, phishing, and Trojan horses, all of which were widely publicized, including those in Estonia, Georgia, Aurora, Stuxnet , Duqa, RSA, and more. Etimad provides the most comprehensive cyber- solution suite available to governments for the implementation of security policies and the protection of national, vital infrastructures from cyber-attacks. A national level solution is essential to state governments in order for them to be able to address the cyber frontier and oversight capabilities, via a proactive approach and a centralized command and control platform. Our cyber security solution offering includes a cyber-intelligence system, a security operations center and a cyber-campaign training simulator, our unified platforms enable the monitoring and prevention of cyber- attacks, enhanced with supreme forensics capabilities, training, and exercise, designed for efficient real time responses and damage control during attacks.

 etimad.ae
etimad.ae
OUR SOLUTIONS
BORDERS SECURITY
BORDERS
In a world where travel and communications cross borders at an unprecedented pace, governments are faced with a formidable challenge: protecting land and maritime borders against threats ranging from illegal crossings, through organized crime and terrorism, to the trafficking of arms, drugs, and people … while still enabling the travel and commerce that are vital to a modern nation. Currently securing thousands of kilometers of borders in a variety of terrains and environments, Etimad’s border solutions provide smart security that safeguards against illegal incursions and activities – while guaranteeing vetted two-way traffic.
UNIQUE VALUE OFFERING
Ongoing adaptive allocation of resources based on hierarchic Command &Control structure, mobile sensing capabilities, and intelligence-driven threat assessment.
Operational optimization based on terrain, weather, and available resources.
Adaptation for land and maritime borders as well as open and closed borders.
Reuse of existing infrastructure and components for optimal ROI and resource utilization.

OUR BORDERS CORE PRODUCTS & CAPABILITIES
Etimad provides Borders solutions adapted for specific border types, terrains, and populations, supported by the following core products and capabilities:
Advanced sensors
Including ground surveillance radars, long range electro-optic devices, smart fence sensors, video content analysis, mobile units, and more.Multi-sensor fusion
Provides stable and continuous tracking of all targets detected while avoiding false or multiple track generation.Auto-slaving of cameras to radar tracks
Automatically positions cameras on a target and moves the camera accordingly.Command and Control (C2)
A hierarchic platform that Integrates fixed, mobile, and handheld units to manage thousands of daily border crossing activities and alerts.UAV (Unmanned Aerial Vehicle)
Provides an immediate up-to-date picture of border sections without deploying security personnel.MSU (Mobile Surveillance Unit)
Adds coverage to fixed deployment and includes sensors, communications and mobile Command & Control capabilities.Patrol vehicles
Provides fast response to illegal border incursions.UGV (Unmanned Ground Vehicle)
Provides remote surveillance and reconnaissance for C&C operators.LAW ENFORCEMENT
Law enforcement has traditionally focused on responsive capabilities - solving crimes and apprehending criminals after the fact. Today, trending and prediction capabilities that have been tried and tested in the commercial arena are recruited to the service of civil society and law enforcement. New systems and platforms provide agencies with tools that harness information from sensors, databases, open sources, the web and the general public – and utilize it to predict criminal patterns and prevent incidents before they occur. Etimad provides law enforcement solutions to numerous countries and agencies, enabling authorities to predict and prevent crime, as well as effectively respond to criminal activities and operations. Our solutions combine the principles of community policing, predictive policing, intelligence-led policing and other proven models to allow for optimal exchange of information between relevant authorities, agencies and the public – and increase the affectivity of law enforcement operations.
UNIQUE VALUE OFFERING
Predictive dispatching based on crime data fusion and analysis
Empowering the public to take an active role in creating a safer environment via our crowd sourcing and citizen advisory bidirectional communication platforms.
Integration of external video management systems (indoor/ outdoor surveillance).
Cross-agency and platform collaboration for improved filtering and correlation capabilities.

OUR LAW ENFORCEMENT SOLUTIONS
Intelligence backbone
Comprehensive, enterprise-level platforms that integrate data systems across an organization, protect data security, and facilitate inward and outward sharing of information.Law enforcement Command & Control
Enables law enforcement authorities to manage thousands of daily policing activities, receive alerts, and generate action recommendations.Real-time crime center
Provides real-time response and management capabilities by integrating and sharing intelligence With forces in the field and with defence and security agencies.Crime prevention platform
Supports law enforcement and international anti-crime agencies in identifying and stopping local, national, and cross-border criminal activities.Urban shield
A unified platform that collects multi-spectral information, analyzes and integrates all collected data, and Provides operational guidance protocols and debriefing analysis capabilities.Safe neighborhood
Provides citizens and authorities personnel with the tools to help report, respond to, and prevent safety and security incidents utilizing mobile phones and other devices such as tablets and laptops.CRITICAL INFRASTRUCTURE
Critical infrastructures, such as energy production facilities, transportation hubs and communication infrastructure are required to ensure the safety and security of employees, assets and the surrounding community –from both internal and external threats. This challenge is complicated by the fact that critical infrastructures are often placed in diverse and remote locations with thousands of employees entering and exiting the facility every day. Etimad critical infrastructure solution are currently securing manned and unmanned sites all over the world, providing maximum protection and safety to the assets, to facility employees, and to nearby civilian population. Our platforms protect onshore, offshore and coastal assets and infrastructures, analyzing fused data from sensors, databases and the web to detect, deter, prevent and manage any breach of security or safety risk.
UNIQUE VALUE OFFERING
Multi-layered safety & security platform combining physical and cyber protection, sensor fusion, intelligence and decision support tools, all correlated in a unified situation awareness picture.
Ongoing adaptive allocation of resources based on hierarchic Command & Control structure, mobile sensing capabilities and intelligence – driven threat assessment.
Operational optimization based on terrain, weather, and available resources.

Flexible, scalable Unified Access Management (UAM) system.
Enhanced crisis management, including employee advisories and dissemination via mobile application.
PRODUCTS AND CAPABILITIES
Etimad provides critical infrastructure protection solutions adapted for specific types of assets, terrains and populations, supported by the following core products and capabilities.
Command and Control (C2)
Utilizes unique fusion and correlation algorithms to evaluate and integrate outputs from the sensor network, control operational components, and enable response initiation and management.Unified Access Management (UAM)
Enables facility operator to monitor and control employee, vendor, visitor and vehicle access and restrict access to different zones based on role or function.Emergency Management Platform
Supports emergency response systems and first responders by integrating existing operational, surveillance and dispatch systems with ad-hoc deployments of mobile sensors and communication components.Smart Facility
Comprehensive facility safety management through the monitoring and control of occupancy, infrastructure and surrounding environment.Crowd Sourcing
Utilizes smartphones to collect information from employees and advise them regarding events and conditions that may affect their safety and well-being.Real-Time Environmental Sensing
Supports facility operators in ensuring compliance with all relevant regulations and standards by providing real-time environmental status.URBAN MANAGEMENT
The 21st century city is characterized by dynamic and growing concerns from multiple domains – from transportation, through resource management, to crime and terrorism. Compounding the complexity Of these challenges are the multitude of stakeholders within the city environments – and their need to coherently manage current requirements, while preparing for whatever challenges will emerge from new technologies, changing geopolitics and the growing urbanization of global population. Currently deployed in china, the middle east and the Netherlands, Etimad urban management solutions offer municipal and national authorities a complete portfolio of products and solutions for effective managements of today’s – and tomorrows – complex urban environment.
UNIQUE VALUE OFFERING
Holistic, integrative approach to management of urban operations and processes.
Integration of multiple domains and cross domain analysis for new insights and multi-agency collaboration.
Utilization of personal platforms (smart phones, tablets, floating car data) for information collection and dissemination.

Enhanced simulation, planning and prediction capabilities for contingency managements, emergency response and risk mitigation.
Reuse of assets / resources such as infrastructure. Sensors and communication networks for faster deployment and cost savings.
OUR URBAN MANAGEMENT SOLUTIONS
Safe city
a holistic platform that channels incoming information from sensors. Databases. Open source platforms, and citizen trustees to generate a comprehensive situation picture and propagate it to safety and security responders.Urban transportation management
integrates real time traffic monitoring and forecasting tools, historic sensor data and advanced analytics to improve driver safety, and reduce congestion and pollution and pollution levels.Emergency response & crisis management
gathers, integrates and processes information from all available sources to provides a functional communication and dispatch network for emergency responders.Environmental monitoring & safety
monitors emission levels water quality and other parameters via a network of fixed and mobile sensors.Integrated urban management
protects critical urban systems from sophisticated cyber-attacks and operational capabilities from disparate city platforms to provide a single – point urban status, analysis and management platform.Urban cyber defense
protects critical urban systems from sophisticated cyber-attacks and increases authority capability to identify. Investigate and prevents attempted cyber-attacks.SAFE CITY
21st century cities are growing rapidly, as over half of today’s word’s population inhabits urban settings, Every day, governments and corporations face new challenges and threats that arise in today’s ever-changing, technologically complex landscape, forcing them to seek new approach to managing public safety, security and well-being, Financial and socio-economic concerns, crime control and community safety are key drivers in pursuing new technologies, operational concepts and the ability to mitigate and contain urban risks and threats. Etimad Safe City solution combines cutting-edge technology, data gathering and analytics capabilities, and advanced modeling platforms to help nations, cities and corporations effectively manage and secure urban environments, reduce crime rates and increase the well-being of its citizens and economic growth.
UNIQUE VALUE OFFERING
Static to Dynamic Approach
Involves adaptive sensing capabilities for optimal and real time operational coverage.Intelligence –Driven System
Includes comprehensive investigation, prediction and prevention capabilities, transforming data into actionable intelligence.Multi-Agency Data Sharing
The Multi-Agency Unified Situational Awareness Picture (USAP) allows efficient management of forces and resources. resulting in greater value to all agencies from an integrated database.
Utilization of Personal Platform
Include smartphones, tablets and floating car data, which connect citizen with Command and Control centers and authorities for information collection and dissemination.Leverage Existing Infrastructure and Assets
Provide cost effective, infrastructure-light, integrated sage city/Law enforcement solution.PRODUCTS AND CAPABILITIES
Advanced Sensors
Include video & audio sensors, LPR, cell phone location, chemical, biological, radiological and nuclear (CBRNE) sensors, PTZ control priority management and sensor allocation to different organizations.Data Center
Equipped with multi-spectral information collection and integration capabilities, providing optimal situation awareness, operational guidance protocols and debriefing tools.Surveillance System
An integrated sensor and advanced analytics suite, whose capabilities include face recognition, object tracking, video and event management, which enable continuous tracking and quick response to incidents and developing events.Command & Control Platform
The heart of the Safe City solution, where all information is received and analyzed to generate a Unified Situation Awareness Picture(USAP) and to manage thousands of daily activities and alerts.3-Dimensional Interior Modeling Tool
TRAFFIC MANAGEMENT
As modern cities grow, geographical distance becomes irrelevant and an increasing volume of vehicles daily overwhelms every nation’s highways, an effective and efficient public transportation system can be immensely significant to a country’s economic growth and well-being. The ability to move large numbers of citizens and travelers within and across cities, swiftly and efficiently, is challenged by increased traffic congestions, long rush hours, pollution, traffic accidents and inefficient response times. Etimad, Intelligent Traffic System provides an integrated real-time view of all transportation elements, including areas of congestion, parking availability and traffic flow, by correlating historic data and future projections, as well as data from existing and dedicated sensors with information-sharing capabilities and multi-agency collaboration.
UNIQUE VALUE OFFERING
Transporting Management System
Enables reduced congestion and lower average trip duration, improved road safety due to a reduced number of incidents and casualties, reduced pollution and improved driver experience.Multi agency collaboration VIA Shared Components and Subsystems
This assists in the optimal use of resources and in the greatest operational efficiency.Enhanced Smart Mobile Sensors Layer for Real Time Traffic Data
User GPS data (from fleets) and cell phone positioning data.
Leveraging Existing Security Infrastructure
Provides cost-effective, infrastructure-light, swift implementation.PRODUCTS AND CAPABILITIES
Sensors Data Collection
Includes fixed and mobile (infrastructure-free), LPR CCTV, RVDS, video analytics and more.ITS Subsystem Integration
Involves video based incident detection and management, variable message signs (VMS), traffic signal control (TSC) and automatic vehicle location (AVL).ITS Command & Control
The heart of the arterial intelligent Traffic System, where all information is received, stored and analyzed, so that resources can be dispatched via predictive capabilities, incident detection, fast responses, optimal route recommendations, dissemination of driver information and a decision support tool.Information distribution module
Conveys and updates real time information, alerts, and recommendations via VMS, radio, smartphones and the Web.CYBER SECURITY
The traditional cyber security methods have become infective, due to the complexity of 21st century cyber communication. modern infrastructure is challenged by modern threats, and cyber –technologies have been recognized as strategic weapons and a means to assault critical national infrastructures and assets. In its simplest terms, cyber –security refers to defenses against electronic attacks launched via computer systems. Operational cyber-security encompasses the full range of threat and vulnerability reduction, deterrence, international engagement, incident response, and resiliency, and therefore, requires effective recovery policies and activities, such as security network operations, information assurance, law enforcement, and intelligence missions as they relate to the security and stability of the global information and communication infrastructure. In our expanding digital world, there are multiple types of cyber-attack that include cyber espionage, the disruption of critical infrastructure, compromised equipment, disinformation propaganda and vandalism, and reconnaissance via target systems (which lead to data leaks and compromised intelligence). There are multiple weapons involved in cyber-attacks, which include botnets, email viruses, spyware, worms, phishing, and Trojan horses, all of which were widely publicized, including those in Estonia, Georgia, Aurora, Stuxnet , Duqa, RSA, and more. Etimad provides the most comprehensive cyber- solution suite available to governments for the implementation of security policies and the protection of national, vital infrastructures from cyber-attacks. A national level solution is essential to state governments in order for them to be able to address the cyber frontier and oversight capabilities, via a proactive approach and a centralized command and control platform. Our cyber security solution offering includes a cyber-intelligence system, a security operations center and a cyber-campaign training simulator, our unified platforms enable the monitoring and prevention of cyber- attacks, enhanced with supreme forensics capabilities, training, and exercise, designed for efficient real time responses and damage control during attacks.
UNIQUE VALUE OFFERING
Regulation & smart enforcement
Outlines policy and standards, risks analyses, disaster recovery plans, product approvals, CERT, and so on.Active Defense and Forensics
Involves investigation on the national level, including active hunting, dedicated vulnerability analysis, and general vulnerability analysis.Cyber intelligence
combines multi – source intelligence and WEBINT systems, storage capabilities, smart engines, and advances rules for gathering information about adversaries and threats.
Training & simulation
This is an end-to –end simulation environment for the training of a national cyber – defense array and troops, security efficiency testing for products and technologies, ongoing evolution of national critical assets safety and security levels. DDOS simulation, insider adversary assaults. network and applications attacks, and so on.National cyber Situational Awareness
Involves the real time monitoring of national cyber assets and ICS.PRODUCTS AND CAPABILITIES
Advanced Sensors
These aid in the understanding of attack sources, and methods, for ICS &ICT environments .IT and SCADA networks (including cyber sensors for passive SCADA, IT and cyber –intelligence). All of which send inputs to a high-kevel security operations center.Security operations center
provides analytic and forensic capabilities and is supported by advanced cyber –intelligence and a unique cyber –campaign training simulator.Cyber collector
Collects raw data from critical networks, using a unique probe, including asset configuration. logs and network capturing (inbound & outbound).A Comprehensive Services Suite
Includes training, policy management. Risk assessment, and process management.Cyber C2 (Command & control) center
This is the core of the national cyber – security suite, and is based on a national grading system and supportive technologies, it enables the collection of information and raw data from various national critical networks, assets and backbones, the detection of anomalies, real time event elaboration and analysis. Cyber events management (emergency and offline) .and a real time national cyber status indicator.Our Solutions – Etimad

طائرة GY300 لإيدح في المعرض (من المصدر)
الثلاثاء 23 يناير 2024 / 11:24
إيدج تعرض 3 مركبات جوية وبرية غير مأهولة متطورة في يومكس وسيمتكس 2024
24 - أبوظبيكشفت "إيدج" المتخصصة في الأنظمة غير المأهولة والمستقلة، ثلاث مركبات جديدة ومبتكرة تسير عن بعد في اليوم الأول من معرض ومؤتمر الأنظمة غير المأهولة يومكس ومعرض المحاكاة والتدريب سيمتكس2024، اللذان يقامان في أبوظبي تحت إشراف الشيخ هزاع بن زايد آل نهيان، نائب حاكم إمارة أبوظبي.
وفي بيان حصل عليه 24 اليوم الثلاثاء، قالت إيدج، إنها عرضتGY300 للإقلاع والهبوط القصير على الأراضي الوعرة وغير المجهزة، وهي طائرة دون طيار، منخفضة الصيانة وعالية الأداء وقادرة على نقل 300 كيلوغرام بكلفة منخفضة.
وأضافت إيدج أنها عرضت أيضاً BUNKER PRO المركبة البرية غير مأهولة المجنزرة وعالية الأداء، للعمليات المستقلة بالكامل مثل المراقبة عن بعد، والاستكشاف، والسير ضمن قافلة، وتحديد الأهداف، والدوريات الخارجية.
أما المركبة الثالثة، M-BUGGY، فهي مركبة برية غير مأهولة ومدولبة للتضاريس المختلفة، وتستخدم أحدث تقنيات التصوير والاستشعار لتوفير بيانات قابلة للتنفيذ للاستخبارات، والمراقبة، والاستطلاع.

إيدج تعرض 3 مركبات جوية وبرية غير مأهولة متطورة في يومكس وسيمتكس 2024
كشفت "إيدج" المتخصصة في الأنظمة غير المأهولة والمستقلة، ثلاث مركبات جديدة ومبتكرة تسير عن بعد في اليوم الأول من معرض ومؤتمر الأنظمة غير المأهولة يومكس ومعرض المحاكاة والتدريب سيمتكس 2024، اللذين يقامان في أبوظبي تحت إشراف الشيخ هزاع بن زايد آل نهيان، نائب حاكم إمارة أبوظبي.
من احدى التغطيات الاعلامية .. وجدت عربة غير مأهولة تدعى ( وشق-1)

للاسف لم اجد صورة كاملة لها ..
تبدو واعدة
الوشق

للاسف لم اجد صورة كاملة لها ..
تبدو واعدة
الوشق

كذلك تبدو - ان لم يخب ظني - درون بيرقدار المخصص للحاملات معروضا في الساحة الداخلية لمعرض يومكس

كذلك تبدو - ان لم يخب ظني - درون بيرقدار المخصص للحاملات معروضا في الساحة الداخلية لمعرض يومكس
مشاهدة المرفق 658256
صورة اوضح
المواضيع المشابهة
- الردود
- 1
- المشاهدات
- 234
- الردود
- 636
- المشاهدات
- 53K
- الردود
- 531
- المشاهدات
- 62K
